Perspective
The perception of fear.

How does one use fear to grow? How does one look at fear & say, "huh, that's actually something I can use as a weapon instead of a crutch". I have been thinking a lot lately.
The perception of fear.

How does one use fear to grow? How does one look at fear & say, "huh, that's actually something I can use as a weapon instead of a crutch". I have been thinking a lot lately.
Concepts on building a distributed ID generator service

As part of day to day operations, systems capture occurrences of events and persist them in data stores. Each of these entries has to be identified uniquely using identifiers or IDs. It's important that these identifiers are unique & can be generated uniquely for the lifetime of the system. Let's explore ways in which we can handle this in distributed systems.
Virtual DOM manipulation with ReactJS
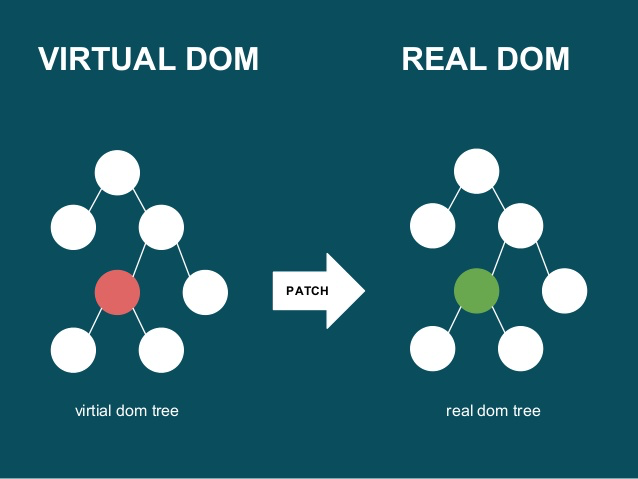
JavaScript is one of the most powerful languages in the current era and it is quickly gaining ground. What makes it powerful is its dynamic nature and ability to manipulate the DOM. This manipulation is at the heart of the modern, interactive web. Unfortunately, it is also a lot slower than most JavaScript operations.
The Vigenere Cipher Broken down in Python
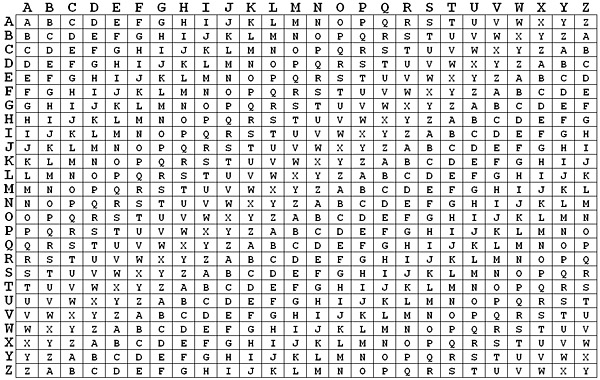
The Vigenere cipher is likely the the most secure ciphers out there. It builds on the principle of the Caesar cipher yet provides a decent way to avoid the easy to solve shift problems. The basic gist of this cipher is we have both a message and a key. The key can be any length, but you must repeat the key for the length of our message to get this to work
The T-shaped developers, A new species of developers
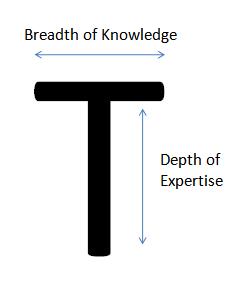
Gone are the days of clear definitions of responsibility, at least in terms of technology and developing software. These are not the times when companies and businesses have clearly defined roles for their employees such that everyone is only closed to the skill set that they deem to be the most proficient in. These are the times when one role for an employee is never going to be enough, or rather is never going to be the case, especially not with how the world is evolving
Difference between Serializable Java interface and Android Parcelable interface

When creating Plain Old Java Objects (POJOs) in eith Android or Java, more specifically Java, the aim is to be able to _model_ our data in a certain way. To enable easier addition to an Adapter or a database, even easier retrieval from a database using **Jackson** library (what Firebase uses to be able to store and retrieve data).
A small demo of configuring a hotspot for your Raspberry Pi

Configuring a Raspberry Pi is fun especially when you delve into IoT and start tinkering around with making machines talk to each other. This tool is perfect for such fun. It is even better when you can get it connected to the internet and perform even more functions such as make your coffee before you wake up or turn off your lights from wherever you are.
Principles governing OOP
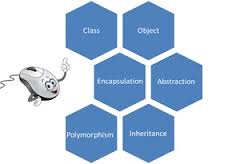
For a program to be said to be object oriented, some principles have to be followed. These principles are crucial to enable the said program to be effective in order to be able to meet the needs the program was designed for.

This post is a demonstration of the difference between post increment and pre increment of variables in Java. Post increment is usually denoted as `x++`, where the x is the variable in question, usually an integer, double or float. While pre-increment is addition denoted as `++x`.
Objected oriented programming
Object Oriented Programming, or as is popularly known in the programming realm OOP is a style of programming that is organized around objects rather than actions.